Session Management in Spring Security
November 26, 2019
Session Management is very crucial part for the Spring Security because if session is not managed properly, then security of data is directly impacted. When we talk about session, some points may come in mind. We need to detect time out. We need to handle concurrent session and session fixation protection. Spring security provides session-management namespace to handle all the session requirements. Here we will understand step by step.
Detect Session Timeout in Spring Security
Once the session is timeout and if someone tries to access then we need to redirect our application on any URL such as login page. Within the session management namespace, we can configure invalid-session-url.<session-management invalid-session-url="/login" >
<logout delete-cookies="JSESSIONID" />
Concurrent Session Control in Spring Security
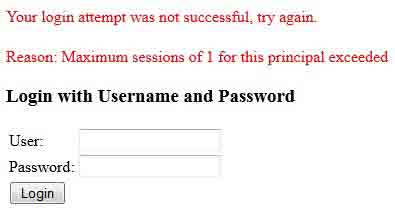
Concurrent session is that one user has more than one session at one time. Here our requirement may vary. We may have the requirement that if a user logins then at the same time no other session is allowed. By default we can open more than one session for one user. Find the concurrency-control namespace to control it.<session-management invalid-session-url="/login"> <concurrency-control max-sessions="1" error-if-maximum-exceeded="true" /> </session-management>
error-if-maximum-exceeded : If the value is true, then Spring Security will show error if maximum session exceeded.
To listen concurrency-control, we need to add a listener in
web.xml.
<listener>
<listener-class>
org.springframework.security.web.session.HttpSessionEventPublisher
</listener-class>
</listener>
Session Fixation Attack Protection in Spring Security
Session Fixation allows one person to fixate session identifier of another person. Attacker does it by sending email with query string. And hence the attacker can access the account of another person. Spring security provides the attributes to avoid the session fixation. In session-management namespace, there is an attribute session-fixation-protection that will handle session fixation.<session-management invalid-session-url="/login" session-fixation-protection="newSession" >
migrateSession : Existing session attributes are copied on new session.
none : Original session will continue and do nothing.
newSession : Creates new session.
With all the configurations, find the spring security xml file.
security-config.xml
<?xml version="1.0" encoding="UTF-8"?>
<beans:beans xmlns="http://www.springframework.org/schema/security"
xmlns:beans="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.springframework.org/schema/beans
http://www.springframework.org/schema/beans/spring-beans-3.0.xsd
http://www.springframework.org/schema/security
http://www.springframework.org/schema/security/spring-security-3.1.xsd">
<http auto-config="true">
<intercept-url pattern="/login" access="ROLE_USER" />
<session-management invalid-session-url="/login" session-fixation-protection="newSession" >
<concurrency-control max-sessions="1" error-if-maximum-exceeded="true" />
</session-management>
<logout logout-success-url="/login" delete-cookies="JSESSIONID" />
</http>
<authentication-manager>
<authentication-provider>
<password-encoder hash="sha"/>
<user-service>
<user name="concretepage" password="0733824cc1549ce36139e8c790a9344d1e385cd2" authorities="ROLE_USER" />
</user-service>
</authentication-provider>
</authentication-manager>
</beans:beans>


